cloudexit (EscapeCloud Community Edition)
cloudexit is an open-source tool that helps cloud engineers perform cloud exit readiness assessments.
It discovers your cloud services, costs, and portability constraints, then generates reports and scores that help you understand:
- where vendor lock-in risks exist,
- what alternative technologies could replace cloud services,
- and how prepared you are for an exit scenario.
cloudexit can run fully offline and is free to use forever.
Optionally, you can connect to exitcloud.io to store assessments and generate advanced reports.
What is cloudexit?
cloudexit is the open-source cloud exit readiness assessment tool from EscapeCloud
It helps cloud engineers understand how difficult (and risky) it would be to exit a cloud provider by generating structured outputs such as:
- Resource Inventory — what cloud services are used and where they run
- Cost Overview — how costs evolved over time and where cost drivers exist
- Risk Inventory — portability constraints and vendor lock-in risks
- Alternative Technologies — replacement options for cloud-native services
- Exit Readiness Score — how prepared you are for an exit scenario (only in Connected mode)
- Vendor Lock-in Score — how mature alternatives are across Human, Technology, and Operational dimensions (only in Connected mode)
cloudexit is designed to be practical and repeatable: you can run the same assessment multiple times, track changes, and use the outputs for planning, risk management, and stakeholder communication.
Exit Strategy
cloudexit supports multiple exit strategies as part of the cloud exit readiness assessment.
An exit strategy describes the target scenario you are planning for (for example, moving repatriating workloads on-premises vs migrating to another cloud provider). The selected strategy helps cloudexit interpret findings and frame recommendations based on a realistic exit path.
In configuration files, this is represented as exitStrategy.
Supported Exit Strategies
| Strategy | Value |
|---|---|
| Repatriation to On-Premises | 1 |
| Hybrid Cloud Adoption | TBD |
| Migration to Alternate Cloud | 3 |
Choose Exit Strategy
If you are unsure which one to choose, start with the strategy that reflects your most likely exit plan:
- Choose Repatriation to On-Premises (1) if you expect to move workloads back to your own infrastructure.
- Choose Migration to Alternate Cloud (3) if you expect to migrate to a different cloud provider.
Note:
Hybrid Cloud Adoptionmay be added in the future.
Why it’s important?
The exit strategy impacts how cloudexit evaluates:
- which services are likely to become blockers in an exit scenario
- portability constraints and dependencies
- the relevance of alternative technologies
- the overall framing of the exit readiness assessment
In other words: it helps translate technical findings into a more realistic exit plan.
Assessment Types
cloudexit supports multiple assessment types as part of the cloud exit readiness assessment.
Assessment types help cloudexit determine what level of dept of analysis and reporting should be generated.
In configuration files, this is represented as assessmentType.
Types
| Type | Value | Description |
|---|---|---|
| Basic | 1 | Works offline. No account or API key required. |
| Standard | 2 | Enables richer scoring and reporting (Connected mode required). |
Basic assessment (offline)
The Basic assessment is designed to work entirely offline.
It typically includes:
- resource inventory
- cost overview
- portability constraints and risk inventory
- baseline reporting
This mode is free to use forever and does not require an account.
Standard assessment (advanced)
The Standard assessment enables more advanced scoring and reporting.
Depending on your setup, it may:
- use enhanced scoring models
- generate richer reports
- allow integration with connected platforms (exitcloud.io / escapecloud.io)
If you are running a connected workflow, Standard assessments require an API key.
Offline vs Connected mode
cloudexit supports two workflows:
Offline mode (default)
Offline mode is the standard cloudexit workflow:
- runs locally on your machine
- connects to your cloud provider using the credentials you provide
- generates reports locally
- stores all results locally under the
reports/directory
Ideal when:
- you want full control over assessment data
- you cannot upload metadata outside your environment
- you want a free and lightweight workflow
Connected mode (optional)
Connected mode allows you to connect cloudexit to:
- exitcloud.io - Lightweight Cloud Exit Readiness Platform for MSPs and SMEs
- escapecloud.io - Cloud Exit Readiness Platform for Enterprises
With connected mode, cloudexit can upload assessment outputs so you can:
- store assessments centrally
- generate richer reports with additional scoring
- compare results across multiple assessments over time
- share and export reports more easily
Ideal when:
- you want assessment history and comparisons
- you run assessments for multiple environments or customers
- you want deeper reporting and scoring models
Quickstart
This guide helps you run your first cloudexit assessment in a few minutes.
1) Clone the repository
git clone https://github.com/escapecloud/cloudexit.git
cd cloudexit
2) Create a virtual environment
python3 -m venv ./venv
source venv/bin/activate
3) Install dependencies
python3 -m pip install -r requirements.txt
4) Run the interactive CLI
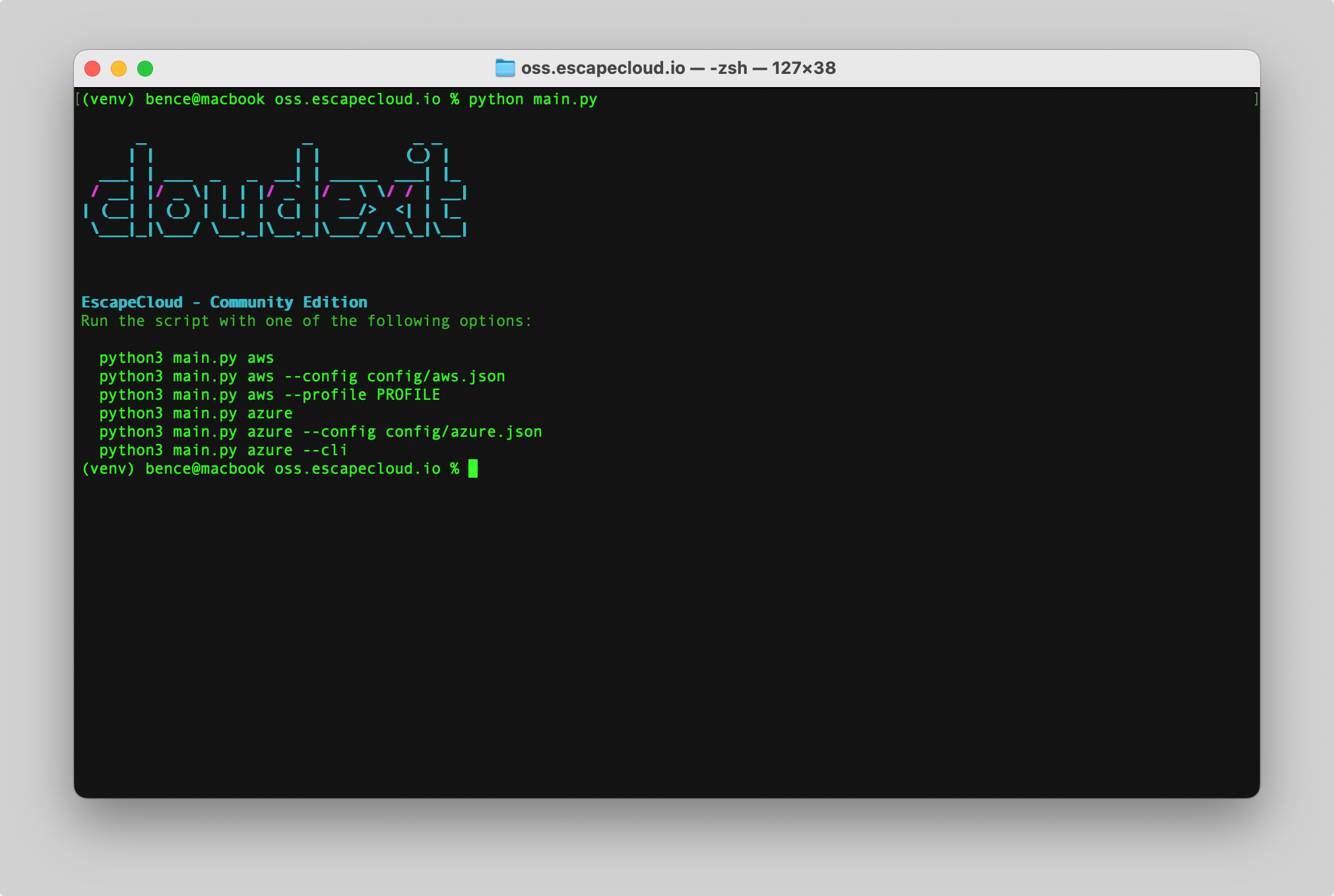
Amazon Web Services (AWS)
python3 main.py aws
Microsoft Azure
python3 main.py azure
cloudexit will guide you through selecting:
- a cloud provider (AWS or Azure)
- scope parameters (AWS Account, region, resource group)
- cloud exit strategy
- authentication method
- assessment type (basic, standard)
- assessment name (optional)
5) Open the generated report
Each assessment creates a new timestamped folder under reports/.
Open the generated index.html or report.pdf file in your browser.
Next steps
-
Configure provider permissions and authentication:
-
Use a configuration file for repeatable workflows:
Prerequisites
cloudexit runs locally and is executed directly from the repository.
Before running the first assessment, make sure your local Python environment is ready.
Python version
cloudexit requires Python 3.10+
Check your version:
python3 --version
Virtual environment & pip
We recommend using a virtual environment to avoid dependency conflicts:
python3 -m venv ./venv
source venv/bin/activate
Then install dependencies:
python3 -m pip install -r requirements.txt
Verify pip is available:
python3 -m pip --version
Common issues
‘python3: command not found’
Install Python 3 using your OS package manager or from python.org.
‘pip install’
Try upgrading pip:
python3 -m pip install --upgrade pip
Virtual environment activation doesn’t work
Make sure you run:
source venv/bin/activate
and confirm you see (venv) in your shell prompt.
Running assessments
cloudexit can run assessments:
- interactively via the CLI (recommended for first-time users)
- via configuration files (recommended for repeatable workflows)
This guide walks you through both.
Interactive mode
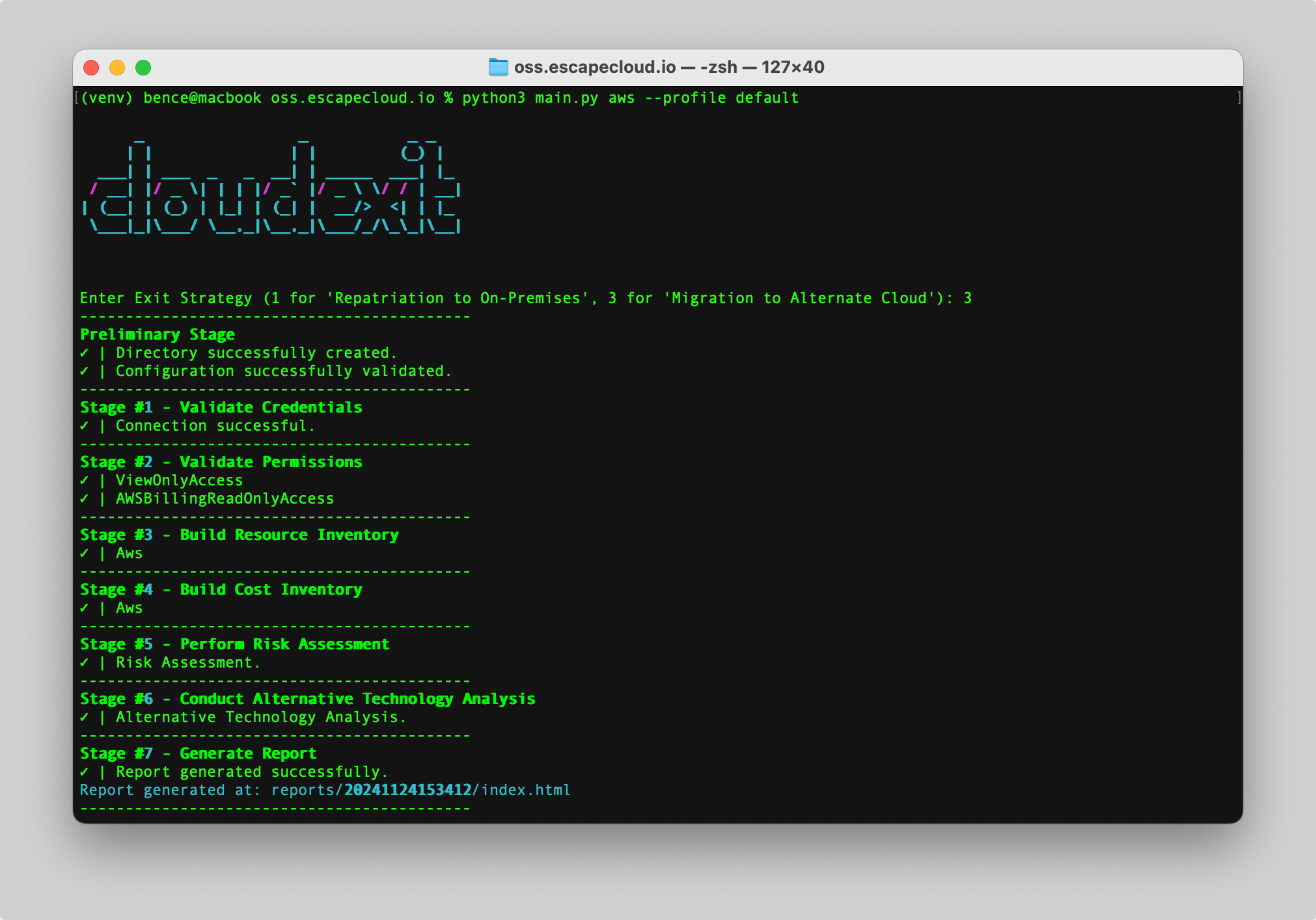
Amazon Web Services (AWS)
python3 main.py aws
python3 main.py aws --profile PROFILE
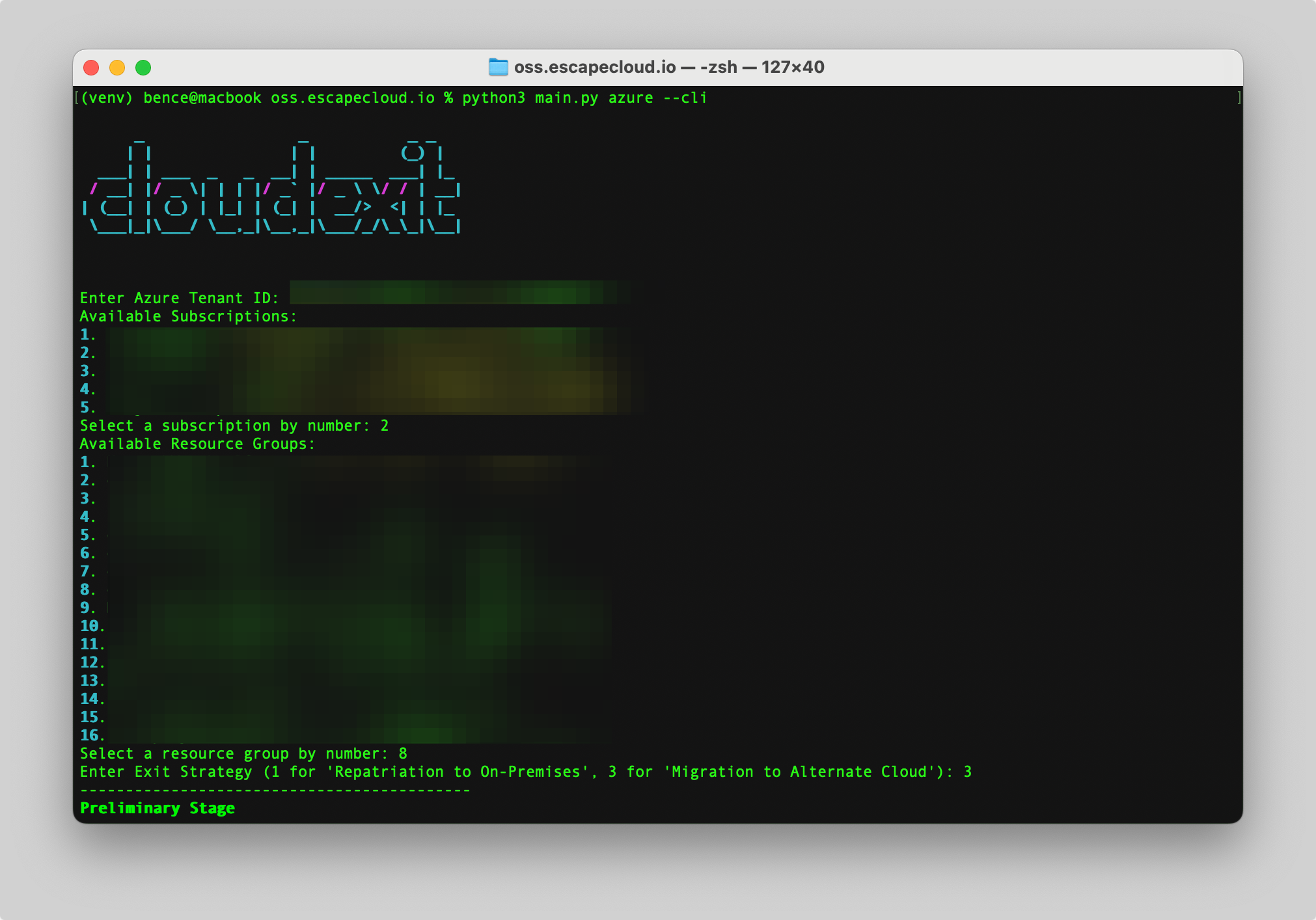
Microsoft Azure
python3 main.py azure
python3 main.py azure --cli
cloudexit will guide you through:
- providing authentication details
- defining an optional assessment name (with the
--nameargument) - selecting scope (based on the cloud provider)
When the assessment completes, cloudexit generates a report folder under reports/.
Configuration file mode
Amazon Web Services (AWS)
python3 main.py aws --config config.json
Microsoft Azure
python3 main.py azure --config config.json
Configuration files are useful if you want to:
- run assessments repeatedly in a consistent way
- automate runs in CI or scripts
- share non-secret configuration defaults across your team
See:
Reports
Each assessment creates a new timestamped folder under reports/.
Typical contents include:
- raw output data
- standardized data
- generated HTML report
- generated PDF report
To view the report, open:
reports/<timestamp>/index.html
Required permissions
cloudexit requires read-only access to discover resources and retrieve cost signals.
If permissions are missing, the most common symptoms are:
- empty or incomplete inventory
- missing cost data
- validation failures during the “Validate permissions” stage
Minimum required permissions
| Cloud Provider | Required Permissions |
|---|---|
| Microsoft Azure | Reader + Cost Management Reader |
| Amazon Web Services | ViewOnlyAccess + AWSBillingReadOnlyAccess |
Principle of least privilege
We recommend using least-privilege credentials:
- avoid overly privileged accounts (e.g., Owner/Admin)
- scope access to only the subscriptions / accounts / projects you intend to assess
cloudexit does not require write permissions.
Troubleshooting permission issues
If assessment fails during:
- Validate permissions
- Build Resource Inventory
- Build Cost Inventory
…double check that the credentials include the required roles/policies above.
Provider-specific guides:
AWS
This page explains how to authenticate cloudexit against AWS and what permissions are required.
Authentication Methods
cloudexit supports:
- Access key / secret key (interactive or config file)
- AWS CLI profiles (
--profile PROFILE)
Required Permissions
To run an AWS assessment, the following AWS managed policies must be attached:
- ViewOnlyAccess (AWS Docs)
- AWSBillingReadOnlyAccess (AWS Docs)
See also: Required permissions
Run an assessment (AWS)
Interactive
python3 main.py aws
cloudexit will prompt you for:
- Exit strategy
- Assessment type
- Access key
- Secret key
- Region
Interactive with AWS Profile
python3 main.py aws --profile default
cloudexit will use credentials from your local AWS CLI config. (AWS Docs)
Azure
This page explains how to authenticate CloudExit against Microsoft Azure and what permissions are required.
Authentication Methods
cloudexit supports:
- Service principal (interactive or config file)
- Azure CLI credentials (
--cli)
Required Permissions
To run an Azure assessment, the following role assignments must be attached:
- Reader (Microsoft Docs)
- Cost Management Reader (Microsoft Docs)
These roles should be assigned at the appropriate scope:
- Subscription (recommended)
- Resource group (supported if you want a narrower scope)
See also: Required permissions
Run an assessment (Azure)
Interactive
python3 main.py azure
cloudexit will prompt you for:
- Exit strategy
- Assessment type
- Tenant ID
- Service Principal / Client ID
- Client Secret ID
Then you’ve to select from the followings:
- Select Subscription Name / ID
- Select Resource Group Name
Interactive with Azure CLI
python3 main.py azure --cli
cloudexit will use your authenticated Azure CLI session. (Microsoft Docs)
Config schema
cloudexit supports running assessments using configuration files.
Configuration files are useful when you want to:
- run assessments repeatedly in a consistent way
- automate runs in CI or scripts
- store non-secret defaults (scope, provider, strategy)
name
Assessment name shown in reports.
Example:
"name": "DMS System"
cloudServiceProvider
Which cloud provider to assess.
| Cloud Provider | Value |
|---|---|
| Microsoft Azure | 1 |
| Amazon Web Services | 2 |
| Google Cloud Platform | TBD |
| Alibaba Cloud | TBD |
exitStrategy
Which exit strategy the assessment should model.
| Strategy | Value |
|---|---|
| Repatriation to On-Premises | 1 |
| Hybrid Cloud Adoption | TBD |
| Migration to Alternate Cloud | 3 |
assessmentType
Which assessment type to run.
| Type | Value | Comment |
|---|---|---|
| Basic | 1 | No API key required |
| Standard | 2 | API key required |
providerDetails
Provider-specific authentication details (varies by cloud provider).
See:
Example structure
{
"name": "DMS System",
"cloudServiceProvider": 2,
"exitStrategy": 3,
"assessmentType": 1,
"providerDetails": {
"...": "..."
}
}
Amazon Web Services (AWS) config
This page shows an example configuration file for running an AWS assessment.
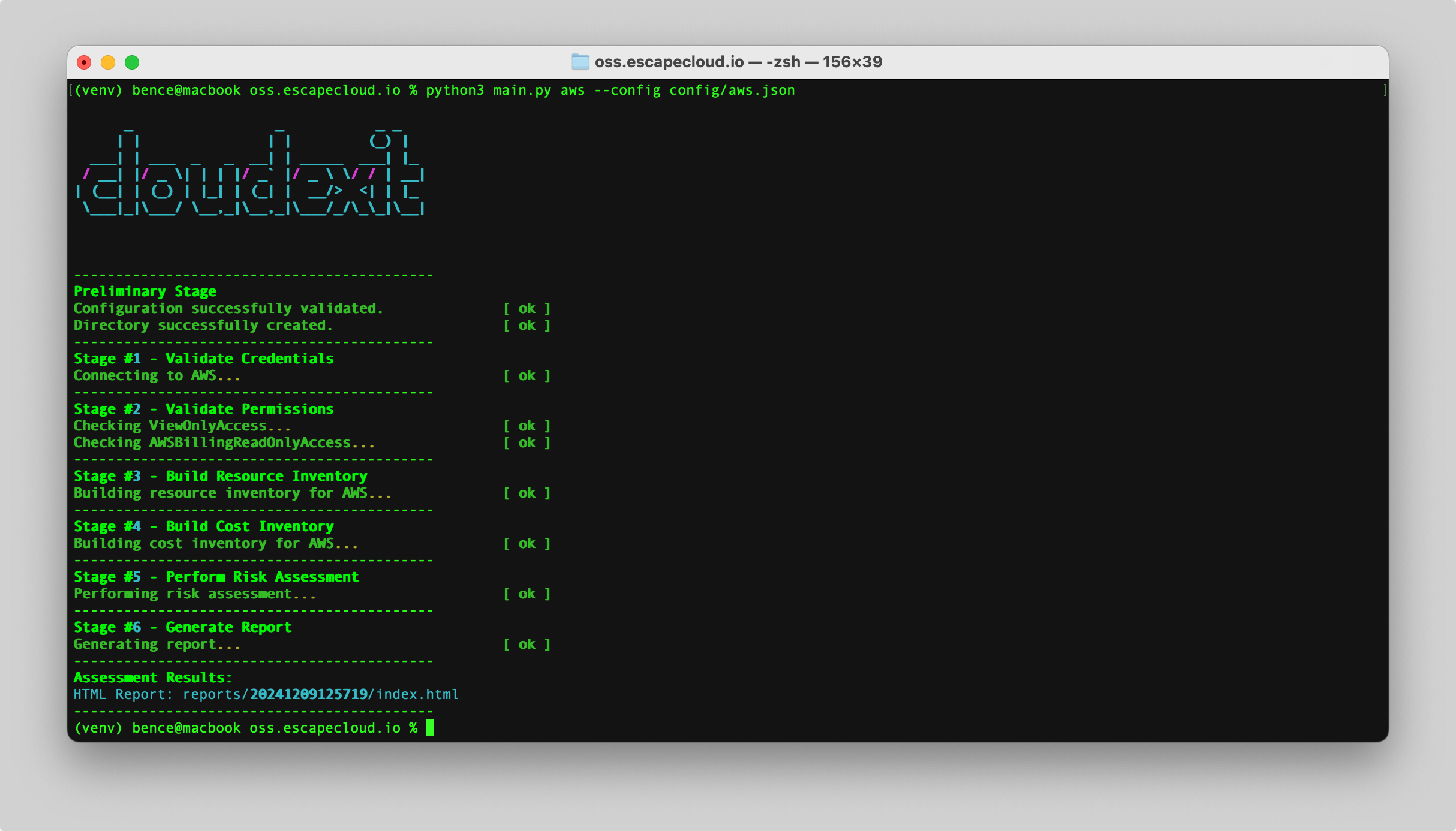
Example AWS config
{
"name": "DMS System",
"cloudServiceProvider": 2,
"exitStrategy": 3,
"assessmentType": 1,
"providerDetails": {
"accessKey": "AKAAXASJHMTOST9YTLHE",
"secretKey": "",
"region": "eu-central-1"
}
}
Run with the config
Save your config (for example as config/aws.json) and run:
python3 main.py aws --config config/aws.json
Notes
- Keep your
accessKeyandsecretKeysecure. - Do not commit real credentials to GitHub.
Microsoft Azure config
This page shows an example configuration file for running an Azure assessment.

Example Azure config
{
"name": "DMS System",
"cloudServiceProvider": 1,
"exitStrategy": 3,
"assessmentType": 1,
"providerDetails": {
"clientId": "a5d7a310-26a4-115f-b679-ca01f0d73b75",
"clientSecret": "",
"tenantId": "38986009-9ded-42b3-b187-55f1cb61560a",
"subscriptionId": "1299bf9a-8ca8-478b-8659-c62e62cd7baa",
"resourceGroupName": "test-project"
}
}
Run with the config
Save your config (for example as config/azure.json) and run:
python3 main.py azure --config config/azure.json
Notes
- Keep your
clientIdandclientSecretsecure. - Do not commit real credentials to GitHub.
Reports Overview
cloudexit generates reports automatically at the end of each assessment.
Reports are designed to help you answer:
- What cloud services are currently in use (Resource Inventory)?
- How costs evolved over time (Cost Overview)?
- Where portability constraints and vendor lock-in risks exist (Risk Inventory)?
- What alternative technologies can replace the services in use (Alternative Technologies)?
- How prepared you are for an exit scenario (Scoring)? (only in Connected mode)
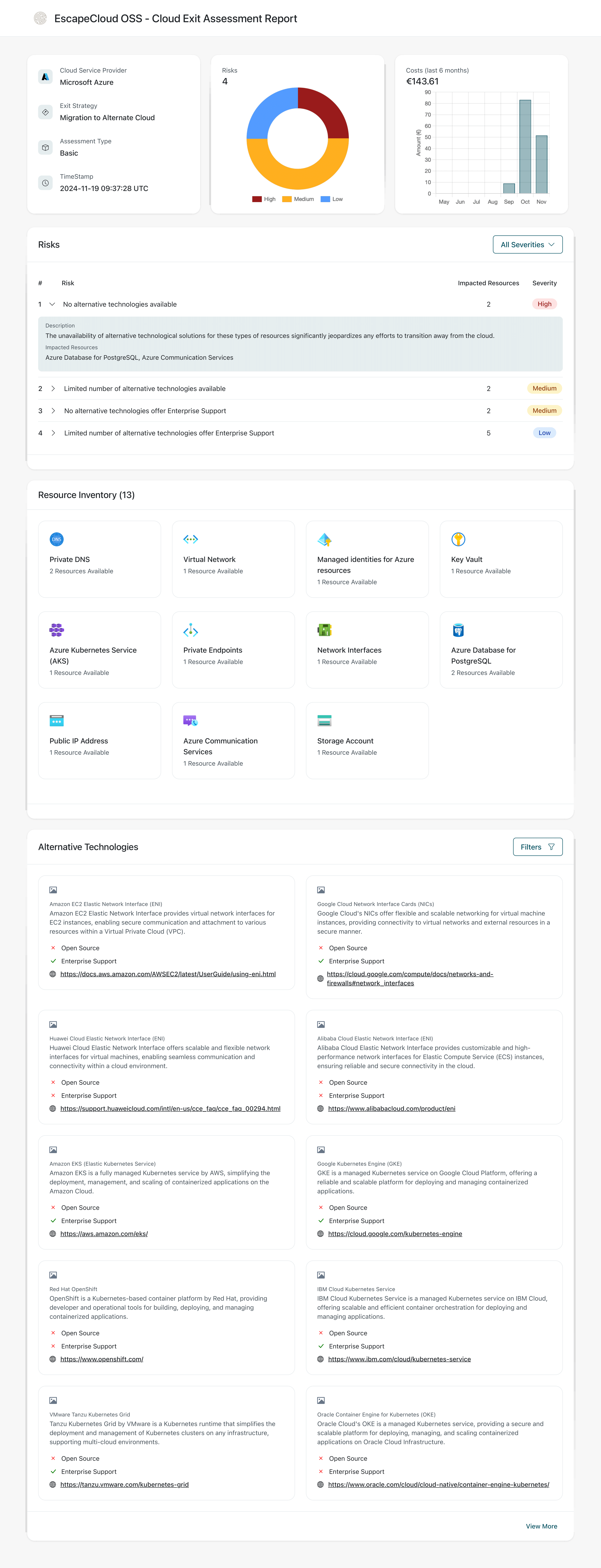
Structure
A typical report contains:
- Resource Inventory
- Cost Overview
- Risk Inventory
- Alternative Technologies
- Scores (only in Connected mode)
Location
Each assessment creates a timestamped folder under:
reports/<timestamp>/
Open the HTML or PDF report:
reports/<timestamp>/index.html
reports/<timestamp>/report.pdf
Formats
Basic (offline)
- Resource Inventory
- Cost Inventory
- Risk Inventory
- Alternative Technologies
- Executive Summary (HTML / PDF)
Standard (only in Connected mode)
- Resource Inventory
- Cost Inventory
- Risk Inventory
- Alternative Technologies
- Scoring
- Executive Summary (on exitcloud.io or escapecloud.io)
- Exit Readiness Report (on exitcloud.io or escapecloud.io)
Resource Inventory
The Resource Inventory summarizes the cloud services identified within the assessment scope.
It answers:
What services are currently in use and how broad is the footprint?
Why it matters
The size and diversity of your inventory often correlates with exit complexity:
- more services usually means more dependencies and migration work
- a larger footprint increases testing, refactoring, and operational change effort
- cloud service provider–specific services might have limited alternatives
The Resource Inventory is also used as input for:
- risk identification
- alternative technology mapping
- scoring (only in Connected mode)
What you will see
Typically, the inventory includes:
- service/resource type (e.g., S3, Lambda, API Gateway)
- number of resources per service type
- location
- totals for the assessed scope
Cost Overview
The Cost Overview shows how cloud spend evolved over time within the assessment scope.
It answers:
What is the financial footprint of the assessed environment?
Why it matters
Costs are important in cloud exit planning because they help you:
- identify expensive dependencies that may become blockers
- estimate the potential cost of parallel-run / migration phases
- support prioritization and stakeholder conversations
If cost data is missing or incomplete, double-check:
- billing permissions
- account/subscription scope
What you will see
Depending on provider capabilities and permissions, cloudexit may show:
- monthly cost trend over a fixed period (commonly last 6 months)
- aggregated totals for the shown period
Risk Inventory
The Risk Inventory highlights factors that may complicate or block a cloud exit and groups them by severity.
It answers:
Where are the main exit blockers, dependencies, and constraints — and how serious are they?
Why it matters
The Risk Inventory is one of the most important sections of the report because it:
- surfaces exit blockers early
- highlights vendor lock-in and portability constraints
- helps you prioritize remediation actions
- provides context for alternative technology analysis
- feeds directly into scoring (only in Connected mode)
Risks should be reviewed together with:
- Resource Inventory (what you have)
- Cost Overview (what it costs)
- Alternative Technologies (what can replace it)
Taken together, these sections form the foundation of a realistic exit readiness assessment.
What you will see
The Risk Inventory typically includes:
- a severity distribution (High / Medium / Low)
- a ranked list of identified risks
- a short description explaining why each risk matters
- impacted resources or services, where applicable
Examples of risks you may see include:
- no alternative technologies available for a service
- limited number of viable alternatives
- lack of enterprise-supported alternatives
- a large or complex resource inventory that increases exit effort
Alternative Technologies
The Alternative Technologies section maps cloud services in use to potential replacement technologies.
It answers:
What could replace the cloud services currently in use?
Why it matters
Alternative availability is one of the strongest signals of exit readiness:
- no credible alternatives for critical services can be an exit blocker
- limited alternatives increases execution risk
- lack of enterprise support can be a blocker in regulated environments
What you will see
For each service type (from the Resource Inventory), cloudexit may provide:
- a list of alternative technologies/products
- short descriptions and links
- filtering (e.g., Open Source, Enterprise Support, Resource Type)
- scoring based on Human / Technology / Operational dimensions (only in Connected mode)
Scores
Scores are available only in Connected mode.
They provide a quantified view of cloud exit readiness based on risks, dependencies, and the alternative technology landscape.
Use scores to:
- communicate readiness clearly
- compare environments over time
- support prioritization and executive decision-making
Exit Readiness Score
The Exit Readiness Score is a combined score reflecting:
- identified risks and constraints
- availability (and, where applicable, maturity) of alternatives
Higher scores generally indicate:
- fewer blockers
- more viable alternatives
- lower portability and lock-in risk
Vendor Lock-in Score
The Vendor Lock-in Score evaluates the alternative landscape across three dimensions:
- Human — skills availability on the market (or hiring/training effort)
- Technology — maturity, stability, feature completeness
- Operational — ecosystem, supportability, third-party services (integrators)
This is often visualized as a radar chart.
Connect to Platform
cloudexit can run fully offline, but you can also connect it to a platform to unlock richer reporting, scoring, and ongoing assessment workflows.
This page explains how Connected mode works for both:
- exitcloud.io (lightweight platform for individuals and SMEs)
- escapecloud.io (enterprise platform, tenant-based)
Why use Connected mode
Use Connected mode if you want:
- centralized storage of assessment results
- richer online reports (PDF)
- scoring and benchmarking (for example Standard assessment type)
- the ability to compare assessments over time
- a platform-based workflow for sharing results
If you only need a one-time offline snapshot, you can stay in Basic (offline) mode.
Requirements
To use Connected mode, you need:
- a platform account (exitcloud.io or escapecloud.io)
- an API key with sufficient credits on the selected platform
- outbound HTTPS connectivity from the machine running cloudexit
Methodology
At the end of a successful local assessment, cloudexit:
- builds a summary payload (resource and cost inventory)
- sends it securely over HTTPS to the configured platform host
- receives an acknowledgement and, for Standard assessments, scoring data generated by the platform
The local HTML report is always generated under:
reports/<timestamp>/
Configuration
Update config.py before running a connected assessment:
# config.py
CLI_VERSION = "v1.0.0"
HOST = "eu.exitcloud.io" # or us.exitcloud.io / <tenant>.escapecloud.io
KEY = "your-api-key"
Generating an API key (exitcloud.io)
- Log in to your regional portal:
- https://eu.exitcloud.io or https://us.exitcloud.io
- Click your user profile (top right corner).
- Select Keys.
- Click New Key and copy the generated key.
Do not modify
CLI_VERSION; it is used for debugging and compatibility tracking.
Credits and limits
Connected mode requires available credits on the selected platform:
- exitcloud.io: credits are scoped per region (EU / US)
- escapecloud.io: credits are scoped per tenant
If no credits are available, cloudexit will still run locally but will not upload results.
Platforms
exitcloud.io
exitcloud.io is available in multiple data regions to support data residency requirements:
| Region | Host |
|---|---|
| EU | eu.exitcloud.io |
| US | us.exitcloud.io |
You select the region by configuring the platform HOST in config.py.
escapecloud.io
escapecloud.io is a tenant-based enterprise platform.
- Each customer has a dedicated tenant:
<tenant-name>.escapecloud.io - The data region is determined by your commercial contract.
- cloudexit connects to the tenant host provided to you.
What gets uploaded
When running cloudexit in Connected mode, only a minimal, structured summary of the assessment is uploaded to the platform.
The goal is to:
- respect data minimization principles
- avoid uploading sensitive information
- enable richer online reports and scoring
cloudexit always performs the basic assessment locally first.
Summary
The uploaded payload contains:
- assessment metadata (timestamps, provider, exit strategy)
- aggregated Resource Inventory
- aggregated Cost Overview
No credentials, secrets, or raw configuration data are uploaded.
Resource Inventory
The Resource Inventory payload contains aggregated counts, not raw resource identifiers.
For each detected resource type, the payload includes:
- resource type identifier
- location/region (if available, otherwise
unknown) - number of resources
Example:
{
"id": 12,
"location": "eu-central-1",
"count": 36
}
Cost Overview
Cost data is uploaded as monthly aggregates.
Each entry includes:
- billing month
- total cost for the month
- currency
Example:
{
"month": "2024-12",
"cost": 1234.56,
"currency": "USD"
}
IMPORTANT
cloudexit does not upload:
- access keys, secrets, tokens, or client credentials
- resource names, ARNs, tags, or IDs
- raw billing line items
- local databases or report files
Offline vs. Online reports
cloudexit supports two reporting modes:
- Offline
- Online (Connected)
Both start from the same local assessment engine.
Offline
Offline mode focuses on a lightweight, self-contained workflow.
You get:
- a local HTML report under
reports/<timestamp>/index.html - sections covering:
- Resource Inventory
- Cost Overview
- Risk Inventory
- Alternative Technologies
Offline reports:
- require no account
- require limited internet connection
- do not include scoring
- are generated once per run
This mode is ideal for:
- exploratory assessments
- one-time reviews
- restricted environments
Online
Connected mode extends the same local run with a platform workflow.
You get:
- richer PDF reports hosted on the platform:
- Executive Summary
- Exit Readiness Report (from ‘Standard’ assessment)
- scoring and benchmarking (only in Connected mode)
Key differences
| Area | Offline (Basic) | Online (Connected) |
|---|---|---|
| Internet required | Yes | Yes |
| Account required | No | Yes |
| Data storage | Local | Local & Platform |
| HTML report | Local | Local & Platform |
| PDF reports | Limited | Executive + Exit Readiness (if Standard) |
| Scoring | No | Yes (if Standard) |
| Continuous assessments | No | Yes (platform-initiated) |
Common errors
This page lists common issues you may encounter when running cloudexit and how to resolve them.
Assessment fails immediately
Possible causes:
- Missing or invalid credentials
- Insufficient permissions
What to check:
- Verify credentials are correct and active
- Confirm required permissions are assigned
- Review CLI output for provider-specific error messages
No resources detected
Possible causes:
- Incorrect account, subscription, or project scope
- Region filtering excludes active resources
What to check:
- Ensure the correct account or subscription is used
- Review region or scope settings in the CLI or config file
Cost data missing or incomplete
Possible causes:
- Billing permissions not granted
- Cost data not yet available for recent periods
What to check:
- Verify required billing permissions
- Confirm the billing period contains usage data
Upload to platform failed (Connected mode)
Possible causes:
- Invalid API key
- No available credits
- Incorrect platform host
- Network connectivity issues
What to check:
- Verify
HOSTandKEYvalues inconfig.py - Confirm credits are available on the platform
- Check outbound HTTPS connectivity
Unexpected errors
If you encounter an error not covered here:
- re-run the assessment with debug logging enabled
- capture the full CLI output
- open an issue in the GitHub repository with details
Authentication & Permissions
Most cloudexit issues are related to authentication or permissions.
Cloud provider authentication
cloudexit supports multiple authentication methods depending on the provider:
- CLI-based authentication (e.g. AWS profile, Azure CLI)
- Configuration file credentials
- Interactive (in terminal)
Ensure the authentication method you use is supported by the selected cloud provider.
Required permissions
cloudexit requires read-only permissions to perform an assessment.
Examples:
- AWS:
ViewOnlyAccess,AWSBillingReadOnlyAccess - Azure:
Reader,Cost Management Reader
Missing permissions may result in:
- incomplete inventories
- missing cost data
- failed assessments
Platform authentication (Connected mode)
Connected mode requires:
- a valid API key
- sufficient credits
- correct platform host configuration
Verify these settings in config.py before running a connected assessment.
Best practices
- Use dedicated read-only roles or service principals
- Avoid using personal admin credentials
- Rotate keys regularly
How to contribute
cloudexit is an open-source project and contributions are welcome.
Reporting issues
When opening an issue, please include:
- cloud provider and region
- assessment type (Basic or Standard)
- CLI version
- relevant error messages or logs
Code of conduct
Please be respectful and constructive when contributing.
License
cloudexit is released under the GNU Affero General Public License v3 (AGPL-3.0).